Learning cyber security has gained more importance due to the changing nature of cyber threats, and incident response is a crucial element in modern IT operations. A detailed cyber security incident response strategy helps professionals understand and learn the nature of cyber attacks and efficiently prepare for potential incidents.
A comprehensive incident response plan includes cybersecurity best practices and detailed playbooks to address the latest cybersecurity threats. Incident response teams that leverage artificial intelligence (AI) in cybersecurity can successfully handle incidents and will be in demand in the job market.
Continuous improvement and ongoing education are key components of the incident response process, and the role of educational programs in advancing cybersecurity knowledge is indispensable. Through extensive and focused cybersecurity training, professionals can comprehend various types of cyber attacks and the latest technologies transforming the cybersecurity landscape.

What Is Cybersecurity Incident Response?
Cybersecurity incident response, or incident response, is the practice of mitigating and addressing cyber attacks. Cyber incident response involves identifying threats, handling attacks, and recovering from the harmful effects of cyber incidents as quickly as possible.
Why Is Incident Response Crucial in Modern IT Operations?
Incident response is crucial in modern IT operations for several reasons, including mitigating attacks, recovering faster from incidents, minimizing damage, reducing costs, saving time and energy, complying with regulations and laws, and enhancing overall security posture.
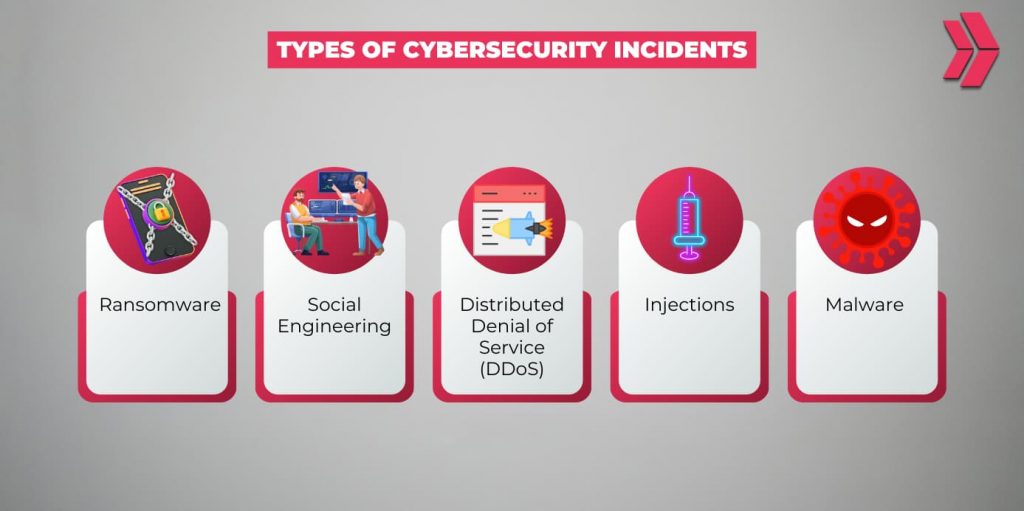
What Are The Types of Cybersecurity Incidents?
Here are the top 5 common types of cybersecurity incidents;
- Social Engineering
- Ransomware
- Distributed Denial of Service (DDoS)
- Injections
- Malware
Social Engineering
Social engineering, or human hacking, is on the rise, and about 90% of all cyber attacks are based on social engineering, according to Avast Q1/2024 Threat Report. Phishing is the most common social engineering technique used to gain initial access.
Ransomware
Ransomware attacks encrypt endpoints or servers and demand ransom to provide decryption keys. The number of reported victims in the first quarter of 2024 increased by almost 20% compared to the same period of the last year, according to the GRIT Q1 2024 Ransomware Report published by GuidePoint Security.
Distributed Denial of Service (DDoS)
A DDoS attack occurs when a large amount of internet traffic from many compromised sources floods a victim’s service and makes it unavailable. It can lead to total crushing of systems, loss of income, and reputation disruption.
Injections
Injection attacks infect the victim with a malicious code or payload. Injection attacks are the third most common type of cyber attack, according to OWASP Top 10:2021. The top 2 primary injection attacks are SQL injection and XSS.
Malware
Malware, or malicious software, is designed to steal, modify, or disrupt sensitive information on computers, networks, and systems. The most common types of malware include trojan horses, worms, and viruses.
What Is an Incident Response Plan?
An incident response plan is a comprehensive documentation of identifying, mitigating, and recovering procedures. It is crucial for reducing impact and recovery time, maintaining business continuity, and eliminating organizational disruptions.
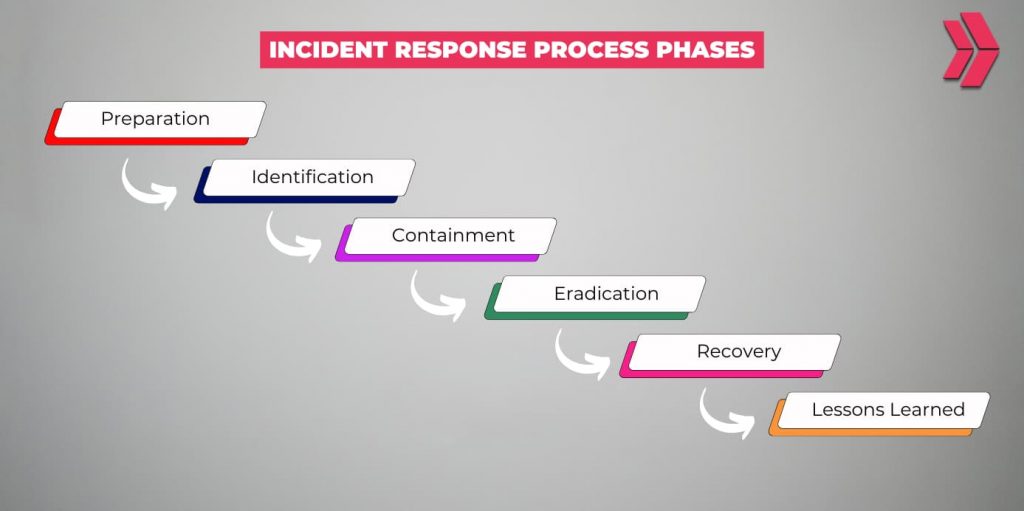
What Are the Phases of an Incident Response Process?
Incident handling procedures require a systematic methodology. Here are the 6 main phases of an incident response process:
- Preparation: Devising incident response plans, managing inventory and resources, and providing user training.
- Identification: Analyzing attacks, assessing impacts, and prioritizing incidents.
- Containment: Applying protective security measures, such as blocking malicious traffic, isolating users or systems, and disabling compromised accounts.
- Eradication: Removing the root cause, checking for any remaining malicious elements, and taking precautions against future attacks.
- Recovery: Restoring systems, ensuring system availability, and providing guidance to relevant parties.
- Lessons Learned: Creating in-depth reports to learn from mistakes, providing IR teams with the latest attack patterns, and updating incident response plans accordingly.
How to Create an Incident Response Plan?
An incident response plan should cover the six phases of the abovementioned incident response process. Later on, a detailed plan should identify the responsibilities and roles of the incident response team. Creating a playbook that follows company policies is also essential, as it clearly explains the steps involved in recognizing, examining, and recovering from cyber attacks. Additionally, it is vital to have a communication plan that includes post-incident activities and notification procedures.
What Roles and Responsibilities Are Essential in an Incident Response Team?
The main job description of an incident response team is to develop a detailed plan, appropriately respond to cyber incidents, and maintain best practices. Nevertheless, as mentioned in the NIST Special Publication 800-61:Computer Security Incident Handling Guide, incident responders may participate in information-sharing procedures, providing education and security awareness training and providing consultancy when required.
The job descriptions and size of the incident response team can vary depending on many factors. However, some critical roles of an incident response team are team manager or team lead, technical lead, threat researchers or analysts, and communications manager.
What Tools and Technologies Enhance Incident Response Capabilities?
Cybersecurity tools and technologies enhance incident response capabilities by supporting human nature. Some popular cybersecurity tools for detecting and responding to threats are SIEM, IPS, EDR, and firewalls. Additionally, vulnerability management tools, SOAR solutions, and AI technologies have revolutionized incident response efforts.
How to Train Your Team for Efficient Incident Handling?
Effective incident handling requires properly training the incident response team and providing updates on the latest developments. Drills and simulations are critical for testing the response plan and training responders. Tabletop exercises are good options that offer cost-effective solutions for training and identifying vulnerabilities in the response plan.
Similarly, red team exercises can simulate real-world attacks to test incident response capabilities. Additionally, professionals should review security exercises and digest lessons learned, which contributes to continuous learning and updating the incident response plan.
How to Continuously Improve Your Incident Response Strategy?
Cybersecurity experts should continually enhance their incident response strategy to improve overall security and effectively combat cyber threats. Professionals should regularly update the incident response plan and provide proper training to the incident response team. Regular drills are also essential to test the readiness of the team and the effectiveness of the response plan.
Why Is Continuous Improvement Necessary in Cybersecurity?
Continuous improvement is essential in cybersecurity for several reasons, including enhancing security posture, adapting to the evolving threat landscape, training security personnel, updating the course of action, and confirming compliance with regulations and standards.
How to Incorporate Feedback into Incident Response Planning?
Incorporating feedback into incident response planning is vital for enhancing preparedness for future threats. Cybersecurity professionals should review post-incident findings and analyze them to learn from the experience. Later, the experiences and lessons learned should be integrated to train the responders and update the incident response strategy.
Conclusion
Security breaches present significant threats to security efforts; thus, incident response is crucial in modern IT operations. Responding to incidents covers processes from identifying threats to recovery of systems. A comprehensive incident response strategy reduces the impact and recovery time, provides business continuity, and protects sensitive digital assets.
To combat cyber attacks, cybersecurity experts should create a detailed incident response plan, train incident responders, utilize the latest incident response tools and technologies, stay informed about new developments, and regularly update the incident response strategy. A cybersecurity analyst course provides the foundation for a robust incident response procedure that can methodologically and systematically handle cyber incidents.
Frequently Asked Questions (FAQs)
What is cybersecurity incident response?
Cybersecurity incident response is the proper handling of cyber attacks. Incident response procedures include identifying, containing, and recovering from cyber intrusions. A comprehensive incident response plan requires continuous improvement to address the latest cybersecurity threats.
How does AI influence modern cybersecurity incident response strategies?
AI is essential in modern cybersecurity incident response strategies to recognize, react, and recover from cyber-attacks. It can process big data and automate tasks. Leveraging artificial intelligence (AI) in cybersecurity offers enhanced threat detection and incident response, improved visibility and reporting, detailed threat intelligence, and assistance in decision-making.
What new technologies are transforming cybersecurity incident response today?
Cybersecurity is an evolving field, and the latest technologies transforming the cybersecurity landscape include AI-driven threat detection and automated response, vulnerability management, encryption, blockchain, cloud security, and threat intelligence solutions for enhanced incident response efforts.
What are the most prevalent types of cyber attacks that organizations face today?
The global cost of cybercrime is on the rise, estimated to be US$9.22 trillion this year, and is projected to increase by 50% by 2028, according to Statista market insights. The 5 most common types of cyber attacks include malware, social engineering, DDoS, injections, and ransomware.
What are the best practices for training an incident response team?
Training incident response teams are of the utmost importance, and here are the top 3 best practices for better incident handling: First, build a detailed incident response plan aligned with ISO, SANS, or NIST frameworks. Second, develop an incident playbook that outlines the possible course of actions of attackers. Third, ongoing cybersecurity training is indispensable in incident response strategy; thus, it utilizes drills and simulations to prepare incident responders.
How can educational programs advance cybersecurity knowledge within organizations?
The cybersecurity field is constantly changing, and the role of educational programs in advancing cybersecurity knowledge is undeniable. Educational programs offer extensive training with a focused curriculum, industry-specific certification in demand, networking with others, cybersecurity best practices, updates on the latest developments, and hands-on experience for enhancing cybersecurity skills.
What are the top cybersecurity best practices?
Cybersecurity best practices are essential in preempting cyber threats and managing potential intrusions. Here are the top 7 cybersecurity best practices: utilize the latest cybersecurity tools and technologies to detect and mitigate attacks, employ encryption technologies, ensure the software is up-to-date and patched, use strong passwords and multi-factor authentication, regularly back up data, comply with cybersecurity frameworks, and provide ongoing education to employees.




