A penetration tester, often referred to as an ethical hacker, conducts authorized simulated cyberattacks on computer systems to evaluate their security. Penetration testing exposes vulnerabilities and helps organizations improve security postures and implement proper security measures. This practice, commonly known as a pentest. Successful penetration testers possess unique hard (technical) and soft skills that allow them to navigate the complex world of cybersecurity. By combining technical knowledge, problem-solving abilities, and ethical hacking techniques, these professionals play a vital role in safeguarding organizations against potential threats.
This comprehensive guide will explore the skills, knowledge, and mindset required to excel in pentest.

What is Penetration Testing?
Penetration testing or pentesting or ethical hacking is a cyber attack performed by trained professionals to identify security vulnerabilities and weaknesses in networks, systems, or applications that threat actors could exploit. In this security testing, testers simulate the real-world tools and techniques that attackers might use.
Why is Penetration Testing Important?
Here are the 5 reasons why penetration testing is important:
- Tests security measures
- Identifies vulnerabilities
- Provides security advice
- Helps to comply with reuirements
- Maintains brand reputation

Tests Security Measures:
The main goal of pen-testing is to validate security measures and corroborate the effectiveness of precautions taken against cyber attacks. Penetration tests are vital to see the readiness of incident response teams.
Identifies Vulnerabilities:
Penetration testing helps discover vulnerabilities that attackers could exploit and prepare risk analysis reports.
Provides Security Advice:
Testers present possible weaknesses in the system and directions on how to improve security posture to prevent future threats.
Helps To Comply With Requirements:
Organizations should comply with industry needs and frameworks to keep themselves up to date and maintain corporate identity. Pentesting helps conduct compliance auditing.
Maintains Brand Reputation:
Reputations take much work and are easy to lose. A successful attack may destroy the reputation and result in financial loss. Robust security protocols could strengthen the trust of customers.
What Does a Penetration Tester Do?
A penetration tester is responsible for simulating real-world attacks on computer systems, networks, and applications to identify vulnerabilities and assess their security posture. The primary role of a penetration tester is to detect vulnerabilities that offenders may exploit, recommend how to improve security and mitigate future attacks. In this context, the penetration tester job description covers 5 steps.
Here are 5 things that penetretion testers do:
- Planning
- Reconnaissance
- Scanning
- Exploitation
- Reporting
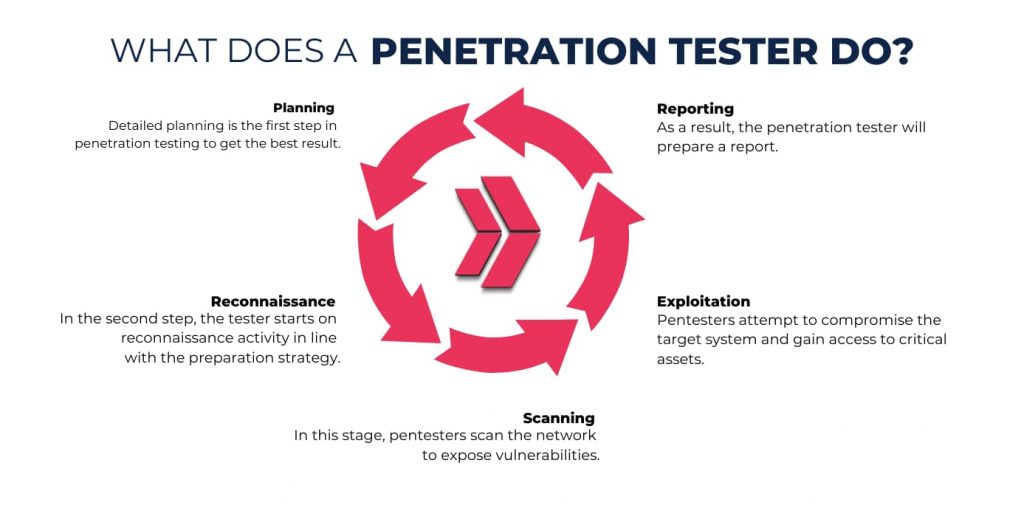
Planning:
Planning is the first step in penetration testing to get the best result. For this, the client and tester should meet to determine the scope of the penetration and target areas to be tested before the project. In this phase, the tester begins to develop a strategy.
Reconnaissance:
In the second step, the tester starts on reconnaissance activity in line with the preparation strategy. First, pentesters gather information about the target and decide what techniques and tools to use. Then, they put all efforts into resolving potential attack vectors for maximum exploitation.
Scanning:
After reconnaissance, the hands-on phase starts. In this stage, pentesters scan the network to expose vulnerabilities. This could involve identifying open ports, services running on those ports, and any system vulnerabilities that could be exploited. Testing tools such as Metasploit, Burp Suite, Nmap, and Wireshark are beneficial in this phase. Additionally, testers will use their manual testing skills such as coding and scripting to bypass intrusion detection systems and encryption mechanisms.
Exploitation:
Exploitation is the harvest time of all efforts. Pentesters attempt to compromise the target system and gain access to critical assets. How far a tester can go may reflect the vulnerability to a cyber attack. The impact of the damage shows the lack of security policies.
Reporting:
Reporting is the final step of testing. As a result, the penetration tester will prepare a report. This report describes the penetration testing methodology and tools used during the project. Additionally, this report generally covers findings about identified vulnerabilities and recommendations for system hardening. Reporting also improves information security.
What Are The Required Skills For A Penetration Tester?
A penetration tester should possess a combination of hard and soft skills to become successful. This part will discuss the required skills for a penetration tester.

What Are The Required Hard (Technical) Skills For A Penetration Tester?
Penetration testers must have a deep understanding of network appliances and the technical background to conduct penetration tests and expose vulnerabilities. Here are some of the technical skills required for a penetration tester:
Ethical Hacking Techniques
Ethical hacking techniques involve the systematic and controlled exploitation of vulnerabilities in computer systems, networks, and applications. Firstly, penetration testers should be familiar with reconnaissance, scanning, enumeration, exploitation, and post-exploitation techniques. Similarly, they must have experience in various methodologies and testing tools to identify and exploit vulnerabilities. Finally, reverse engineering techniques and tools are widely used for penetration testing.
Networking Protocols
Networking protocols are a set of rules and conventions that govern how data is transmitted, received, and processed across computer networks. Penetration testers should understand network functions well to analyze network communication. Within this scope, networking protocols like TCP/IP, DNS, DHCP, SSH, and HTTP are paramount to identifying possible vulnerabilities.
Programming Languages
Pentesters should be creative in infiltrating into systems. They should have comprehensive knowledge of programming languages like Ruby, Perl, Bash, and Python to write scripts to automate tasks. Even “script kiddies” may penetrate systems to some extent. However, programming language knowledge distinguishes professional pentesters from script kiddies.
What Are The Top Required Soft Skills For A Penetration Tester?
The top required soft skills for a penetration tester are communication, analytical thinking, and adaptability.
Communication
Communication is vital for successful penetration. Lack of communication between the tester and client may lead to failure. Also, testers should handle audiences, either technical or non-technical, tactfully and explain technical concepts. Moreover, testers provide concise reports to organizations to improve information security.
Analytical Thinking
Analytical thinking refers to the ability to systematically break down complex problems, analyze information, and draw logical conclusions based on evidence and data. As a result of reconnaissance, the tester might have much information. However, testers problem-solving and analytical thinking skills could successfully assess the exposed vulnerabilities. Gathering data is a hard job, but analytical thinking is what makes this info meaningful.
Adaptability
Adaptability refers to the ability to adjust, modify, or change one’s approach, behavior, or mindset in response to changing circumstances, new challenges, or unexpected situations. Firstly, since technology constantly evolves, penetration testers should adapt to changing environments and situations. Likewise, pentesters should adjust their approach quickly when faced with unexpected penetration testing challenges during the project. The nature of penetration tester jobs requires working under pressure in challenging situations.
What Are 3 Penetration Testing Methodologies?
3 penetration testing methodologies are black, white, and gray box testing. Penetration testing methodologies are the procedures to achieve maximum benefit and meet all requirements during the test process. The choice of methodology changes according to the situation that is being tested.

What is Black Box Testing?
Black box testing is a methodology in which testers have no prior knowledge about the target other than an URL or IP address. This penetration methodology is acknowledged to be the most realistic simulation of an attack. This methodology simulates an attack from an external source, like a hacker. This security testing provides flexibility to use various techniques to expose vulnerabilities in the system. Pentesters sometimes use malware analysis to infiltrate systems or to defeat target defense.
What is White Box Testing?
White box testing, also known as clear box testing, transparent box testing, or structural testing, is a method of software testing that tests internal structures or workings of an application, as opposed to its functionality. In white box testing, an internal perspective of the system, as well as programming skills, are used to design test cases.
White box penetration testing methodology provides all necessary information about the network security or the system before the test. This kind of security testing simulates an insider threat like an employee, former employee, or contractor with knowledge or access to the system. A white box testing strategy is a good option for the prospect of insider attacks. Testers may focus on specific targets with limited scope to identify security weaknesses. Keep in mind that secure code review focuses on source code and does not test physically, and different from white box testing.
What is Gray Box Testing?
Gray box testing is the “gray area” between black box and white box testing. Testers are provided with sufficient knowledge about the code or internal functionality, but not full knowledge, to identify vulnerabilities. This methodology is generally used for insiders with limited knowledge or access to the system.
What Are Penetration Testing Tools?
Security professionals use penetration testing tools to enhance efficiency and improve capabilities. However, manual analysis techniques sometimes are inadequate in identifying vulnerabilities, so automated software programs are used to support manual testing methods.
Also, penetration testing tools help understand how threat actors can exploit networks or systems. The combined use of different tools will produce better results for comprehensive testing. Plenty of free and paid penetration testing tools list exist in the market.
What Are The Popular Penetration Testing Tools?
Popular penetration testing tools are Metasploit, Burp Suite, Nmap, and Wireshark. More information about this popular penetration testing tool is following:
What is Metasploit?
Metasploit is a popular open-source penetration testing tool. This penetration testing framework executes and develops exploits. It has a comprehensive library of pre-built modules, payloads, and exploits that facilitate identifying weaknesses. In addition, the user-friendly interface of Metasploit enables people of all experience levels to use it efficiently to test systems.
What is Burp Suite?
Burp Suite is not an open-source which offers a free edition for users. This vulnerability scanner performs web application testing. It provides automated dynamic scanning options and enhanced manual testing. Burp Suite is one of the best penetration testing toolkits in the industry.
What is Nmap?
Nmap is an open-source penetration testing tool for network scanning, security auditing, and host discovery. Nmap, or Network Mapper, maps the network’s entire wired and wireless security and finds open services and ports which may lead to further exploitation by attackers. Additionally, Pentesters or real attackers get the operating system detection and service version scanning with the help of Nmap to gain access to the target.
What is Wireshark?
Wireshark is a free and open-source penetration testing tool. This network protocol analyzer captures packets and then analyzes the network traffic in real-time. In addition to pentesters, other threat offenders use Wireshark to identify vulnerabilities and exploit sensitive data such as financial transactions, emails, passwords, and credit card information. Moreover, Wireshark can also be used in troubleshooting network problems.
What Are The Vulnerability Scanning Tools?
Vulnerability scanning tools are software programs that expose potential vulnerabilities in networks and systems. Popular vulnerability scanning tools are Nessus and OpenVAS. More information about this popular vulnerability scanning tool is following:
What is Nessus?
Nessus is an open-source vulnerability network scanner. This remote security scanning tool scans for potential threats. Nessus conducts port vulnerability scans for weaknesses and provides detailed reports and recommendations.
What is OpenVAS?
OpenVAS is an open-source vulnerability assessment scanner that checks services and visible ports. OpenVAS can be customized to meet the required needs to scan databases, applications, networks, and systems to detect weaknesses.
What are Social Engineering Tools?
Social engineering tools are designed to simulate social engineering attacks, such as pretexting, baiting, and phishing. Popular social engineering tools are SET and BeEF. More information about this popular social engineering tool is following:
What is SET (Social-Engineer Toolkit)?
SET is an open-source toolkit to simulate social engineering attacks. Testers may use a variety of attack vectors, such as payload delivery, credential harvesting, and phishing.
What is BeEF (Browser Exploitation Framework)?
BeEF is also an open-source social engineering tool that assesses web application security. This tool enables attackers to test for vulnerabilities on the client side. The target’s browser is used as an attack point to expose vulnerabilities.
How To Become A Penetration Tester?
Penetration testing offers a rewarding and exciting career. You can have in-house or remote penetration tester job opportunities.
Here we will discuss the core requirements and skills to become a penetration tester:
Education and Certification Pathways
Junior penetration tester jobs require to have a background in the IT and cybersecurity fields. A pentester should have basic scripting, coding, programming, exploit development, and operating systems knowledge in this context. In addition, a penetration tester can have a four-year regular college degree or a certificate to succeed in the field.
Formal Education and Degrees
The first option is a bachelor’s degree in computer science, information technology, cybersecurity, or related areas. Traditional college education provides comprehensive knowledge that is required in the market. A degree will be a plus and could stand out applicants in job hunting.
The second option is to have a penetration testing certification with the help of a cybersecurity bootcamp. Bootcamps offer penetration testing courses with a focused curriculum, including theoretical knowledge and hands-on exercises that simulate real-world scenarios.
Industry Certifications
Both free and paid cybersecurity certifications are available to support your career. Here we will mention some globally recognized certificates that help you get penetration tester jobs.
CEH (Certified Ethical Hacker)
EC-Council offers CEH (Certified Ethical Hacker) program designed to identify and exploit vulnerabilities. The certification covers various topics like scanning, reconnaissance, and exploitation to meet the requirements of an entry-level penetration tester.
CompTIA PenTest +
CompTIA offers PenTest+ certification, which is a combination of theoretical knowledge questions and performance-based questions. In this context, hands-on assessment questions test the analysis scanning and vulnerability assessment skills.
OSCP (Offensive Security Certified Professional)
Offsec Academy offers OSCP (Offensive Security Certified Professional) certification and introduces penetration testing methodologies with Kali Linux. This certificate validates practical penetration testing skills.
GIAC GPEN (Global Information Assurance Certification Penetration Tester)
GIAC Corporation offers GIAC GPEN (Global Information Assurance Certification Penetration Tester) certification for a junior penetration tester. This certificate proves its holder has a solid foundation and technical skills to conduct penetration tests successfully.
Training and Workshops
In addition to formal education and certifications, many training courses and workshops are available to learn new skills and techniques.
Bootcamps or other training programs organize mini boot camps or short workshops to help students develop some skills in vulnerability assessment, network penetration testing, and web application security.
Building Your Portfolio and Gaining Experience
A robust cyber security portfolio will validate your knowledge, skills, and experience in the field.
Participating in bug bounty programs
Bug bounty programs help you gain practical experience in penetration testing. Moreover, bug bounty programs are a great way to earn money and build a strong portfolio. Companies or organizations offer rewards to expose vulnerabilities in their systems.
Open source projects and contributions
Penetration testers may contribute to open-source projects. These kinds of projects are essential in gaining experience and building portfolios simultaneously. In addition, contributing to open-source projects indicates sufficient knowledge and expertise in the field.
Capture the Flag (CTF) competitions.
CTF competitions simulate real-world scenarios and are challenging for candidates. In addition, CTF activities force penetration testers to be creative and enhance their competitive spirit. Consequently, CTFs help build strong portfolios.
Job Hunting and Networking
Effective and efficient strategies are essential in job hunting efforts to land a job quickly.
Job search strategies
There are several effective approaches to job search strategies to consider. Firstly, having a solid penetration tester resume highlighting your experience and skills is critical. Additionally, job search websites are good options for finding openings. Moreover, direct communication with recruiters or the company could increase the chance of getting hired. Finally, make your detailed preparation for penetration tester interview questions.
Networking and professional associations
Networking is vital in the industry because your visibility and reputation will increase. When you attend an event or a conference, you have a chance to connect with others. These connections may pave the way for your future job.
Online communities and forums
Online communities and forums keep participants updated with the latest developments and enhance networking opportunities. Pentesters can learn from each other, share knowledge and gain experience, and you can find a job.
Final Words
As a result, pentesters are essential to identify and help fix vulnerabilities. Therefore, there is a growing demand for skilled penetration testers.
Penetration testing offers a rewarding cybersecurity career with many advantages. An ethical hacker who keeps up-to-date with the latest developments and strives to improve required skills will always be badly needed in the industry.
Building a robust foundation is vital to becoming a successful penetration tester. So, keep improving yourself for a promising career and a bright future.
Frequently Asked Questions
What is the salary range for a penetration tester?
According to Glassdoor, the median estimated annual penetration tester salary is $97,671. However, penetration testing salary ranges, including experience, skills, location, education, and certifications, can vary. The most Likely Range is between $75K and $128K. Overall, the penetration testing salaries are satisfactory and establish a work-life balance successfully.
How can I transition from another IT field into penetration testing?
Firstly, you should have comprehensive knowledge of cybersecurity fundamentals. Later on, having penetration tester certifications will validate your competence in the field. Then, practical education is needed to demonstrate your skills. Bootcamps, focusing on hands-on training that helps gain experience, are good options to get proper training and land a cybersecurity job quickly.
What are the career development opportunities for a penetration tester?
Pentesting offers a rewarding and challenging cybersecurity career with high satisfaction because you help others keep systems or networks safe and improve security posture.
In the report published by MarketsandMarkets in 2022, the global penetration testing market was estimated to be about $1.4 billion last year and is forecasted to reach $2.7 billion by 2027. Moreover, cloud security is becoming increasingly important daily, and so are job openings.
Cybersecurity jobs are on the rise, and there is a growing demand for skilled pentesters. The U.S. Bureau of Labor Statistics forecast a 35% increase in job growth until 2031.
Penetration testing career provides various job roles in different industries. For instance, you may specialize in an area and improve in this subject. Or, you can continue your career in management roles. Additionally, self-employment, or security consulting, is another option to follow.
What is the difference between a penetration tester and a vulnerability assessor?
Basically, vulnerability assessors and penetration testers are responsible for identifying vulnerabilities. Although used interchangeably, penetration testing vs. vulnerability scanning is different from each other.
Vulnerability assessors utilize automated scanning tools to identify, classify and report security weaknesses. Vulnerability assessments can be carried out regularly, for example, once a month. Besides, even the company’s cybersecurity personnel can conduct a vulnerability assessment in addition to third-party contractors. Also, vulnerability assessors do not attempt to exploit vulnerabilities.
On the other hand, penetration testers combine testing tools and manual skills to exploit vulnerabilities and gain access to targets. It is generally acknowledged to perform pen-testing at least once a year by professional third-party penetration testing companies. Furthermore, penetration testers have more extensive knowledge and experience in cybersecurity and penetration than vulnerability assessors.
Are there any legal risks associated with penetration testing?
Yes, there are legal risks concerning penetration testing. Before conducting any test, testers should obtain written permission; otherwise, all activities can be deemed illegal. In addition, data availability, confidentiality, and integrity should be protected during penetration testing, or the tester could be accountable for possible troubles. Over and above, testers should document all activities and share findings thoroughly. Digital forensics plays a crucial role in penetration testing.




