In a world where cybersecurity has become a paramount concern for businesses and individuals alike, effective log management and investigation serve as the bedrock of a strong security framework. This article aims to elucidate the concepts and practices involved in Windows log investigation using Splunk, a leading platform for operational intelligence. We explore the foundational elements such as the concept of a log, what constitutes a cybersecurity event, the nature of Windows Event Logs, the Event Viewer, and Windows Event IDs. Moreover, we present a case study that brings these concepts to life by demonstrating the detection and investigation of Windows failed login attempts in Splunk. Whether you’re a system administrator, a cybersecurity enthusiast, or someone interested in the workings of Windows logs and Splunk, this article provides insights that can enhance your understanding and application of cybersecurity practices.
What is Log and Why is Important?
A log refers to a record or entry of events, actions, or messages that occur during the execution of a program, system, or process. It is used for troubleshooting, debugging, and monitoring purposes. Logs are typically stored in text files, databases, or other logging systems. Developers and system administrators often analyze logs to identify errors, track system behavior, or gain insights into the performance and functionality of a system.

Logs can contain various types of information, such as error messages, warnings, status updates, timestamps, user actions, and more. They are crucial for diagnosing issues, auditing activities, and understanding the sequence of events that led to a particular outcome.
What is Cyber Security Event?
A cybersecurity event is any occurrence or observable incident that has the potential to impact the security of computer systems, networks, or data. These events are often monitored, detected, and logged by various security systems and tools.
A cybersecurity event can include the following:
- Intrusion attempts: These events involve unauthorized individuals or entities trying to gain unauthorized access to systems or networks, often through methods like hacking, brute-force attacks, or exploiting vulnerabilities.
- Malware infections: Events related to malware involve the detection or presence of malicious software, such as viruses, worms, trojans, ransomware, or spyware, on a system or network.
- Data breaches: A data breach event occurs when unauthorized individuals gain access to sensitive or confidential information, potentially resulting in the exposure or theft of that data. This can include personal information, financial records, intellectual property, or trade secrets.
- Network anomalies: Events related to network anomalies involve suspicious or abnormal activities within a network, such as unusual traffic patterns, network scanning, or attempts to bypass security controls.
- System vulnerabilities: Events related to system vulnerabilities are indicators of weaknesses or flaws in software, hardware, or configurations that could potentially be exploited by attackers.
- Security policy violations: Events related to policy violations occur when users or systems deviate from established security policies or guidelines, such as unauthorized access attempts, improper data handling, or misuse of privileges.
- Security system alerts: Security systems, such as intrusion detection and prevention systems (IDPS), firewalls, or antivirus software, generate events when they detect potential threats or suspicious activities. These events can help in identifying and responding to security incidents.
It’s important to note that cybersecurity events are not limited to the above examples and can vary widely based on the specific security measures in place and the nature of the threats faced by an organization or system. Effective monitoring, detection, and response to cybersecurity events are crucial for maintaining the security and integrity of computer systems and networks.

What is Windows Event Log?
The Windows Event Log is a built-in feature of the Microsoft Windows operating system that records and stores a variety of system, security, and application-related events. It serves as a centralized repository for logging and tracking important events and activities occurring within a Windows system. The Event Log helps system administrators, developers, and security professionals monitor, diagnose, and troubleshoot issues on Windows-based computers.
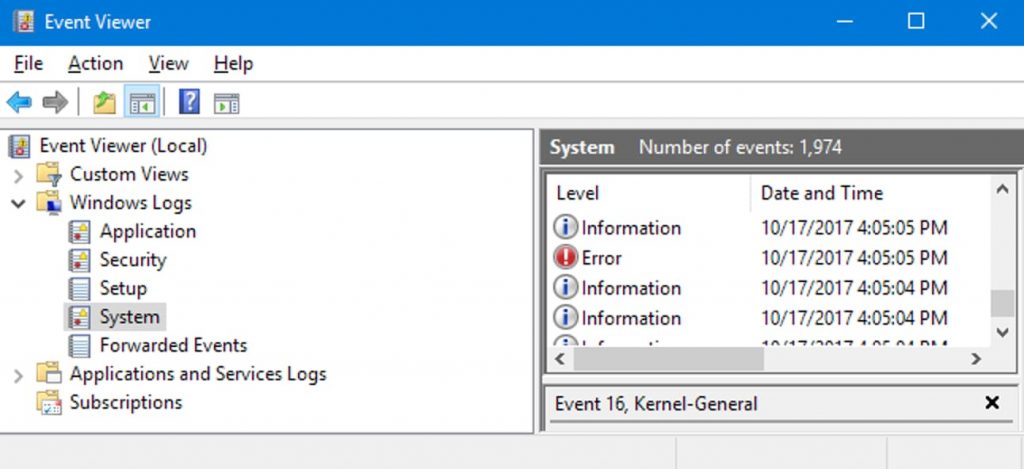
What is Windows Event Viewer?
The Windows Event Viewer is a built-in Microsoft Windows utility that allows users to view and manage the event logs recorded by the Windows operating system. It provides a graphical user interface (GUI) for accessing and analyzing the logs stored in the Windows Event Log. The Windows Event Viewer is a powerful tool for system administrators, IT professionals, and developers to monitor and troubleshoot issues, analyze system behavior, detect security incidents, and gain insights into the events occurring within a Windows system.
What is the Role of Windows Event IDs?
The role of Windows Event IDs is primarily in identifying, tracking, and managing the various events that occur within a Windows operating system. In the Windows Event Viewer, each event that is logged in the event logs is assigned a unique identifier called an Event ID. The Event ID helps to categorize and identify specific types of events, making it easier to locate and analyze them.
Event IDs are numeric values associated with different types of events, such as errors, warnings, informational messages, or audit events. The Event ID, along with other event details, provides important information about the nature of the event and can assist in troubleshooting and diagnosing issues within the Windows operating system.
Event IDs are defined by Microsoft and are specific to the Windows operating system and its components. Different versions of Windows may have different sets of Event IDs, and third-party applications and services running on Windows can also generate their own custom Event IDs.
Here are a few examples of common Event IDs in Windows:
- Event ID 4624: This event is generated in the Security log when a user successfully logs on to a Windows system.
- Event ID 6005: This event is logged in the System log when the Windows system starts up.
- Event ID 4720: This can be useful for auditing purposes, ensuring accountability, and monitoring account creation activities within a Windows system. It allows system administrators and security professionals to keep track of the creation of privileged user accounts and maintain control over administrative access to the system.
Case Study : Detection and Investigation of Windows Failed Login Attempts in Splunk
In this section, we delve into a practical application of Windows log investigation in Splunk. We examine a real-world scenario involving the detection and investigation of failed login attempts on a Windows system. This case study aims to illustrate how theoretical knowledge can be translated into practical solutions for detecting and responding to potential cybersecurity threats. You’ll learn how to navigate and use the Security Log in the Event Viewer, how to identify and filter relevant Event IDs, and ultimately, how to monitor and investigate suspicious login activities using Splunk. This hands-on exploration offers valuable insights into the practical utilization of Windows logs and Splunk in maintaining robust cybersecurity.
How to Detect Failed Login Attempts in Windows?
To detect failed login attempts in Windows, you can use the built-in Windows Event Viewer or security monitoring tools. Here’s a general approach:
- Navigate to the Security Log: In the Event Viewer, expand “Windows Logs” on the left-hand side, and click on “Security.” The Security Log contains events related to security, including login attempts.
- Event IDs: Enter the relevant Event IDs for failed login attempts. Common IDs include 4625 (logon failure) and 4771 (Kerberos pre-authentication failed).
By monitoring failed login attempts, you can identify potential brute-force attacks, unauthorized access attempts, or misconfigured user accounts. Regularly reviewing these logs and responding to suspicious login activity can help enhance the security of your Windows system.
Investigating Windows Failed Login Attempts using Splunk
Investigating logs from windows event viewer is a challenging task. In real life, windows logs are sent to SIEM tools. Log investigation is performed in these tools. In our example, we sent the logs to Splunk via forwarder. We performed Event ID = 4625 filtering to display the failed login attempts we have made in Splunk.
For example, within 1 minute, we can generate an alert if any Windows user enters the wrong password 5 times or more. Write index=”wineventlog” EventCode=4625 as SPL and save as alert and make the following settings. Thus, when our Windows users make more than 5 failed logins within 1 minute, alerts will start to appear in the Splunk.
Conclusion
Today, the importance of Windows event logs is high in terms of security. It helps us to fix the problem in case of any security breach. In this article, after explaining the concepts of log and event, we talked about the concepts of Windows event ID and event viewer. We have explained a few of the important Event IDs. Then we transferred the logs to Splunk from a computer with Windows operating system. We made several failed login attempts. When we filtered the logs with the 4625 event code, we observed that they were transferred to Splunk successfully. Then, in order to detect brute force attacks, we made the necessary settings to create an alert when there are 5 or more failed login attempts within one minute.




