In the evolving digital landscape, cyber threats have become increasingly complex and severe. More than ever, organizations need robust cybersecurity measures to protect their operations, data, and infrastructure. Enter Endpoint Detection and Response (EDR), a crucial solution that helps detect and neutralize these threats. This article delves into the intricate workings of EDR and illustrates its importance through the lens of a zero-day attack – the Follina vulnerability. We’ll discuss this exploit’s nature, its detection, and investigation using a premier EDR system, CrowdStrike Falcon. Stay with us as we take you through a riveting journey of cybersecurity and the mechanisms in place to counteract these looming threats.

What is Endpoint Detection and Response (EDR)?
Endpoint Detection and Response (EDR), also known as endpoint detection and threat response (EDTR), is a cybersecurity solution that continuously monitors end-user devices to detect and respond to cyber threats like ransomware and malware. This sophisticated system plays a crucial role in today’s rapidly evolving digital landscape, providing the necessary tools to counteract the increasing complexity and intensity of cyber-attacks.
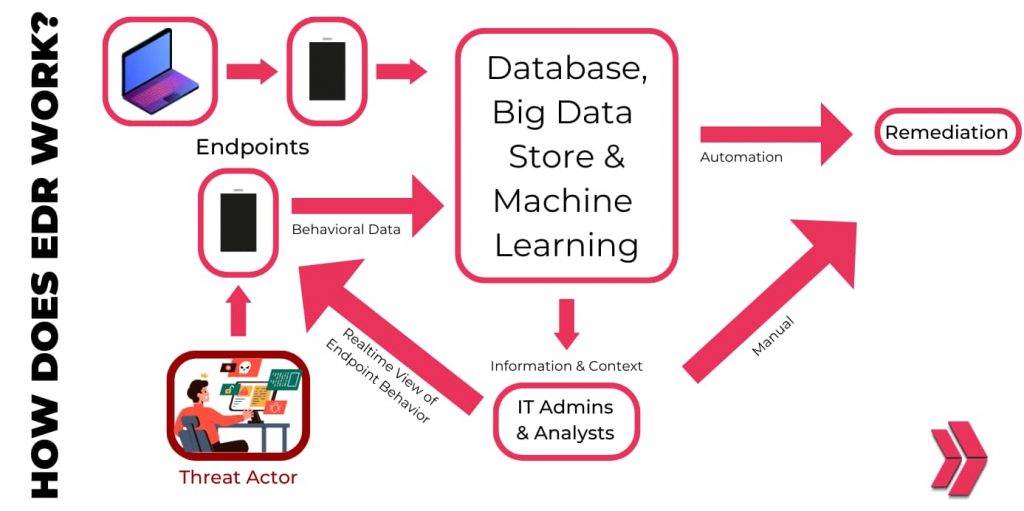
How Does EDR Works?
EDR works by identifying threats on your organization’s endpoints and responding to them accordingly. It can analyze the nature of the threat and provide your IT team with pertinent information regarding how it was initiated, where it has traveled to, what it is currently doing, and most importantly, how to halt the attack entirely. This provides a proactive approach to cybersecurity, allowing organizations to act swiftly and decisively against potential breaches.
What is a Zero Day Attack?
A zero-day attack is an exploit that takes advantage of a zero-day vulnerability. The term “zero-day” refers to the number of days since a new piece of software was released to the public. In this context, “zero-day software” was obtained by hacking into a developer’s computer before release, thus being exploited on “day zero” of its existence.
What is the Follina Vulnerability?
The Follina vulnerability—known as CVE-2022-30190—is a remote code execution (RCE) vulnerability that affects the Microsoft Support Diagnostic Tool (MSDT) in Windows. A remote, unauthenticated attacker could exploit this vulnerability to take control of an affected system. This vulnerability allows exploitation of Windows Support Diagnostic Tool via MS Office files. Microsoft has since released a patch in June’s Patch Tuesday cumulative update to mitigate the impact of this exploit.
What is the Role of msdt.exe in the Follina Vulnerability ?
msdt.exe is Microsoft’s Diagnostic Troubleshooting Wizard. This tool has existed in “C:\Windows\System32” since the release of Windows 7. In previous versions of Windows (XP and Vista), this function was performed through the browser with an ActiveX add-on. This executable became a point of interest due to its role in the Follina vulnerability.
How to Exploit msdt.exe in a Microsoft Office Document?
Exploiting the Follina vulnerability involves a series of steps. The attacker initiates the attack by sending an email containing a malicious Microsoft Office document to the targeted user. This document references an external HTML file which uses the ms-msdt URL protocol to execute PowerShell code. The nature of this exploit underscores the importance of practicing safe email habits and being cautious when opening unfamiliar documents.
Case Study : Detection and investigation of follina vulnerability
Detection of follina in CrowdStrike Falcon
The CrowdStrike Falcon sensor is equipped with detection and prevention logic that effectively addresses the exploitation of this vulnerability. With “Suspicious Process Blocking” enabled, Falcon will block code execution attempts from msdt.exe. Even without this feature enabled, Falcon will still generate a detection in the console, alerting the team of potential threats.
Investigation of Follina in CrowdStrike Falcon
CrowdStrike Falcon platform protects customers from exploits like Follina by using behavior-based indicators of attack (IOAs). This means it analyzes the behavior of processes and system calls on a machine to identify suspicious activity. Through this method, Falcon can effectively counteract even zero-day exploits, making it a valuable asset in any organization’s cybersecurity toolkit.
Conclusion
EDR systems are critical in today’s cybersecurity landscape due to the increasing sophistication of threats that can penetrate edge security. The Follina vulnerability, for instance, highlights the importance of having robust EDR systems like CrowdStrike Falcon in place. With EDR, you can detect, contain, and eliminate threats even if they have managed to infiltrate the perimeter of your system. Therefore, investing in EDR solutions is not just a proactive measure but an absolute necessity for organizations to protect their digital assets and ensure the continuity of their operations.




