
AWS SysOps Administrator Associate Certification Guide & Tips
The AWS Certified SysOps Administrator – Associate Certification is one of the AWS certifications that verifies an individual’s knowledge of deploying, managing, and keeping operational
Reinvent Yourself

The AWS Certified SysOps Administrator – Associate Certification is one of the AWS certifications that verifies an individual’s knowledge of deploying, managing, and keeping operational

The AWS DevOps Engineer Professional Certification stands as a key indicator for professionals successfully driving cloud-centric processes. The certification validates expertise in crucial domains, encompassing
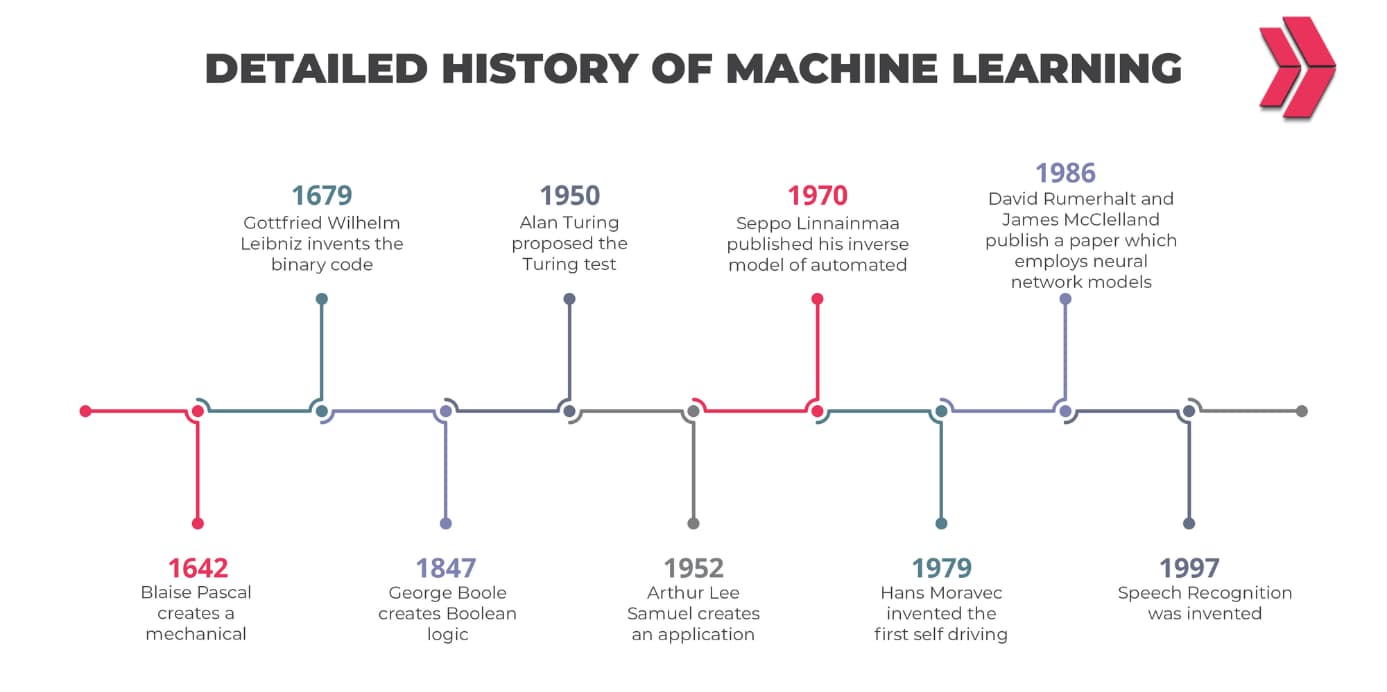
In today’s world, the term “machine learning” is on the tip of nearly every tech enthusiast’s tongue. It’s the driving force behind virtual assistants, self-driving

In today’s rapidly evolving world, pursuing a fulfilling and rewarding career often necessitates embracing change and new opportunities. Meet Furkan, a determined individual who transitioned

In the digital era of 2024, cybersecurity is more than a buzzword—it’s a crucial shield against the ever-evolving landscape of cyber threats. With an estimated

AWS Certified Developer – Associate Certification is a comprehensive program for those who wish to demonstrate their skills and knowledge in using AWS Services to

AWS Solution Architect Professional Certification is an advanced-level credential offered by Amazon Web Services (AWS). If you’re an aspiring cloud architect or an IT professional

In today’s rapidly evolving digital landscape, the Salesforce platform stands as a cornerstone for countless businesses seeking to optimize their customer relationship management (CRM). With
In a world where cybersecurity has become a paramount concern for businesses and individuals alike, effective log management and investigation serve as the bedrock of

In the evolving digital landscape, cyber threats have become increasingly complex and severe. More than ever, organizations need robust cybersecurity measures to protect their operations,