Amidst the marvels of technological advancements, cyber threats require constant attention and watchfulness. To fortify the digital landscape against the ever-changing spectrum of cyber attacks, professionals must uphold a state of continuous vigilance and remain well-versed in the latest cybersecurity risks.
Learning cybersecurity enables practitioners to understand and prepare for a cybersecurity threat and manage the related risks. Cyber threats present both familiar adversaries and novel challenges, each necessitating comprehensive awareness and proactive countermeasures. Notably, the pivotal emergence of AI and quantum computing demands meticulous scrutiny as integral components in this ongoing endeavor.
In this context, the categorization of cybersecurity threats in the present climate and newly emerging threats anticipated for this year will be addressed. Specifically, the role and impact of AI, a key driver of evolving cyber threats, will be covered. Furthermore, the best practices and technologies for mitigating cyber attacks and safeguarding the digital environments for 2024 and beyond will be explored.

What are Cybersecurity Threats?
Cyber security threats are activities that may steal, modify, or disrupt data, systems, or networks. They can adversely affect data and systems’ confidentiality, integrity, and availability. A cyber threat is the potential for an attacker to exploit a vulnerability.
What are the Types of Cybersecurity Threats?
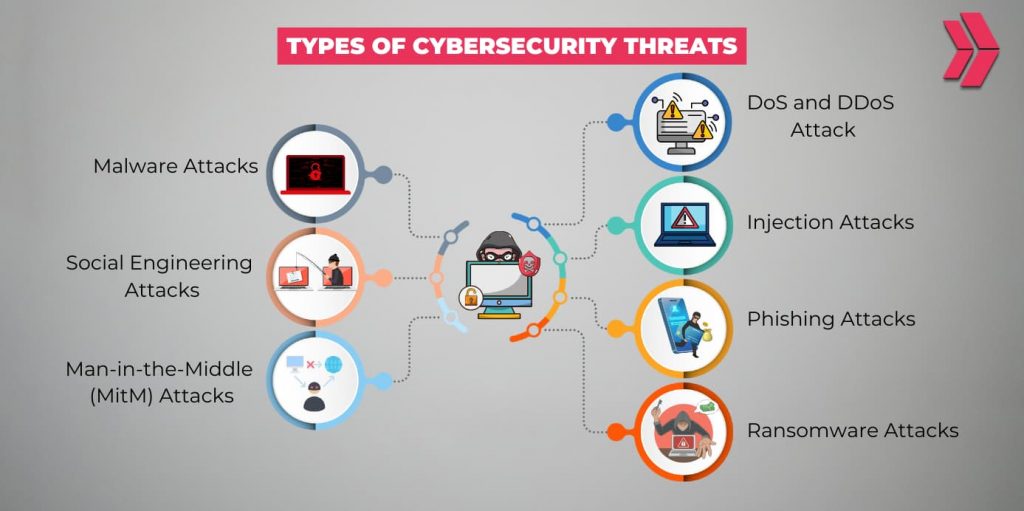
Individuals and organizations need to be aware of a wide array of cybersecurity threats. Here are the most common 7 cybersecurity threats:
- Malware Attacks
- Social Engineering Attacks
- Man-in-the-Middle (MitM) Attacks
- Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
- Injection Attacks
- Phishing Attacks
- Ransomware Attacks
Malware Attacks
Malware, or malicious software, is any code or program designed to harm the target. It is an umbrella term encompassing the most common types of trojans, viruses, worms, rootkits, keyloggers, and spyware. According to CyberArrow Research, malware accounted for 40% of data breaches in the previous year, indicating a 30% increase compared to the year before.
Social Engineering Attacks
Social engineering, or “human hacking,” manipulates human behavior to deceive victims into divulging sensitive information. Interestingly, 98% of cyberattacks are related to social engineering, according to Purplesec research.
Man-in-the-Middle (MitM) Attacks
A man-in-the-middle (MitM) attack, or on-path attack, refers to the eavesdropping process in which attackers position themselves within the network traffic to monitor, steal, or impersonate communication between two parties.
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks:
A denial-of-service (DoS) attack is a malicious activity that disrupts regular traffic by overwhelming the target with a flood of internet traffic. In contrast, a distributed denial-of-service (DDoS) describes malicious attacks using multiple sources, while a DoS attack originates from a single source.
Injection Attacks
Injection attacks exploit vulnerabilities and insert malicious input into a query or code to execute remote commands to read, modify, or change data in the target. Cross-site scripting (XSS) and SQL injection attacks are the most common types of injections, according to the OWASP Top 10.
Phishing Attacks
Phishing emails are one of the most common ways for attackers to gain unauthorized access. While phishing falls under the category of social engineering techniques, it is often highlighted separately due to its significant impact. Nearly 90% of all cyber attacks are initiated by phishing, according to CISA.
Ransomware Attacks
Ransomware, a form of malware, involves cyber attackers encrypting data or restricting system access and demanding payment to restore functionality. This type of attack is widespread. Last year, 10% of organizations experienced ransomware attacks globally, a 33% increase over the previous year, according to the 2023 Check Point Research.
What Are the Emerging Cybersecurity Threats This Year?
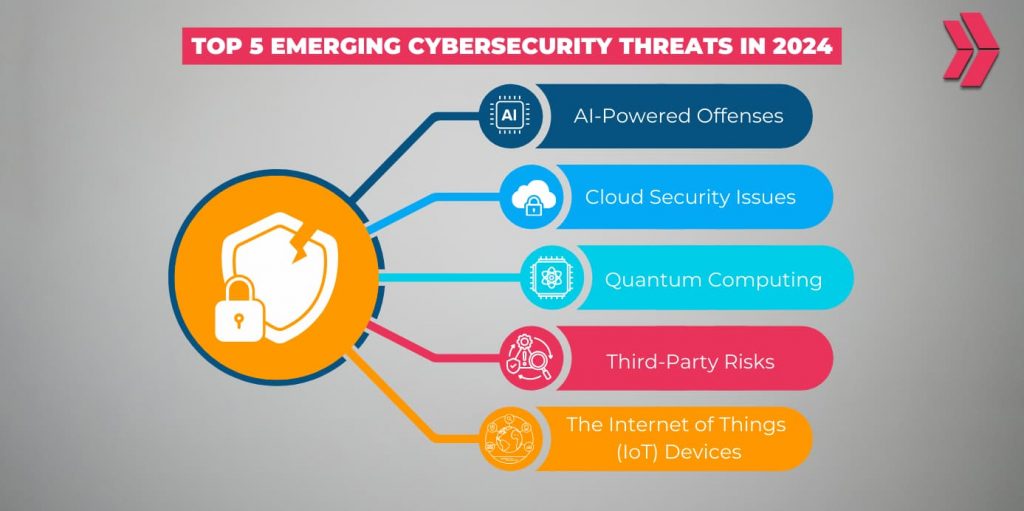
As technology advances, the type and sophistication of threats that must be dealt with also increases. Here are the top 5 emerging cybersecurity threats in 2024:
- AI-Powered Offenses
- Cloud Security Issues
- Quantum Computing
- Third-Party Risks
- The Internet of Things (IoT) Devices
AI-Powered Offenses:
Attackers use artificial intelligence to launch sophisticated cyber attacks, including advanced phishing and ransomware, which account for many cases individuals or organizations face.
Cloud Security Issues:
Nowadays, many organizations are moving to the cloud for different reasons. However, cloud computing has its own security concerns and threats, such as misconfiguration, external data sharing, insecure Interfaces/APIs, or unauthorized accesses.
Quantum Computing:
Quantum Computing rapidly advances and poses a threat to bypass cybersecurity measures. For instance, a quantum computer built by Google in 2019 solved a computation in just three minutes, which supercomputers would take in 10,000 years.
Third-Party Risks:
Individuals and organizations get services from third-party vendors for different reasons. As a result, supply chain or third-party vendors may cause serious cyber threats and cost the target time, money, and resources.
The Internet of Things (IoT) Devices:
The Internet of Things (IoT) devices are in every part of daily life. However, there are some security issues to consider, such as unpatched systems, API vulnerabilities, default or weak passwords, and lack of visibility.
What Role Does AI Play in New Cybersecurity Threats?
Artificial Intelligence (AI) significantly impacts cybersecurity, enhancing defense mechanisms and enabling more advanced attacks.
AI is a force multiplier in cybersecurity efforts. It helps strengthen cybersecurity by improving threat detection and response, automating routine tasks, and learning from past incidents to enhance detection capabilities. It also aids in building a resilient environment and protecting against cyber threats.
On the other hand, AI-powered attacks present a significant cybersecurity threat due to their ability to develop increasingly sophisticated and targeted strategies. Specifically, AI-driven phishing and ransomware attacks have become more convincing, and advanced tools can rapidly identify and exploit vulnerabilities.
What Are Effective Strategies to Guard Against Cybersecurity Threats?
To effectively mitigate the risks associated with cybersecurity threats, it is crucial to prioritize user training, stay informed about emerging threats, and implement multiple layers of security measures. Continuous monitoring and the establishment of efficient incident response plans are also essential. Furthermore, implementing robust authentication methods, such as multi-factor authentication, will enhance cybersecurity efforts.
What Are the Best Practices for Preventing Cyber Attacks?
Cybersecurity professionals can enhance their organization’s security posture and reduce the attack surface by applying some cybersecurity best practices. For instance, providing user training and complying with cybersecurity frameworks such as the NIST Cybersecurity Framework or ISO 27001 are the basics for creating a secure environment. Moreover, employing Multi-Factor Authentication (MFA), using layered security tools for protection, backing up critical data regularly, and applying update and patch management are efficient best practices for preventing cyber attacks.
What Tools Are Essential for Cybersecurity in 2024?
Cybersecurity tools are essential for organizations to protect from cyber-attacks and maintain operational continuity. These tools facilitate real-time threat monitoring, detection, and response, contributing to effective risk management and system hardening.
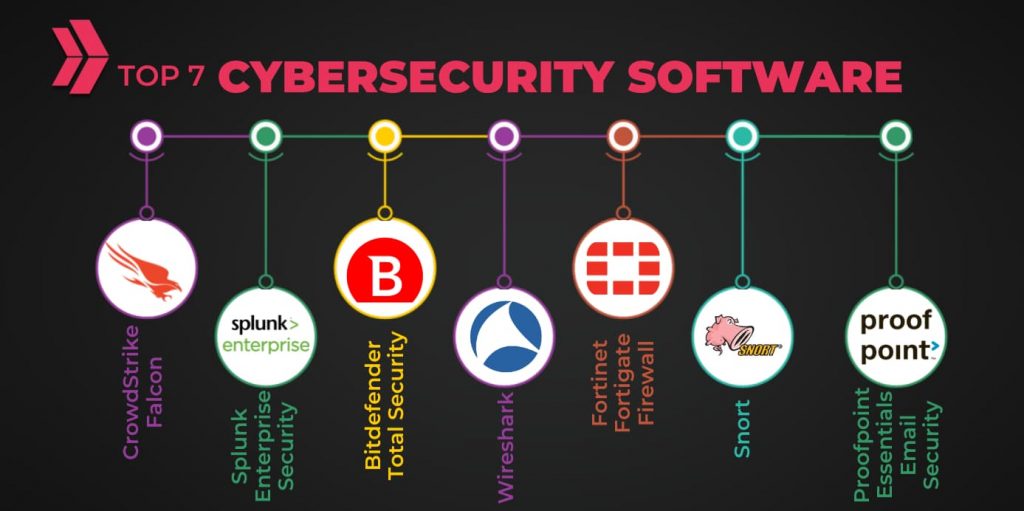
Moreover, they ensure compliance with regional and international standards and laws. A diverse array of cybersecurity solutions exists within each functional category. Here are the 7 most crucial cybersecurity software:
| Category | Cybersecurity Software |
| Security Information and Event Management (SIEM) | Splunk Enterprise Security |
| Cloud-based endpoint protection. | CrowdStrike Falcon |
| Anti-malware software | Bitdefender Total Security |
| Email security and protection | Proofpoint Essentials Email Security |
| Network intrusion prevention system | Snort |
| Next-generation Firewall (NGFW) | Fortinet Fortigate Firewall |
| Network protocol analyzer | Wireshark |
Frequently Asked Questions About Cybersecurity
Here are the frequently asked questions about cybersecurity threats.
What Are the Most Common Types of Cyber Attacks?
In today’s increasingly volatile digital landscape, cyber threats are growing in complexity and severity. Attackers employ sophisticated techniques to breach networks and systems. While the types of cyber attacks are extensive, they can be broadly classified into four primary categories: malware, social engineering, DDoS attacks, and injection attacks.
How Are Latest Technologies Transforming Cybersecurity?
Integrating cutting-edge cybersecurity technologies is imperative to address emerging threats and safeguard the digital environment. Among the latest technologies transforming the cybersecurity landscape are artificial intelligence, context-based authentication, hybrid clouds, quantum computing, blockchain, zero trust policy, and comprehensive threat management.
Why Is Continuous Cybersecurity Education Important?
Continuous cybersecurity education is crucial for 4 main reasons. First, it empowers professionals to protect organizations from cyber attacks and stay informed about emerging threats. Second, ongoing learning equips cybersecurity practitioners to approach risk management and adhere to industry regulations proactively. Third, it helps to create a culture of security awareness within the organization. Fourth, continuous cybersecurity education facilitates professional career advancement.
What Are the Benefits of Cybersecurity Training?
Cybersecurity training is essential in establishing a robust security posture, mitigating risks, and protecting valuable digital assets. Cybersecurity training offers numerous benefits, including enhanced security awareness, advanced technical competencies, adherence to regulatory requirements, efficient incident handling, preservation of reputation, and cost-effectiveness.
Can AI Like ChatGPT Be Used in Cybersecurity?
Nowadays, it is widely recognized that artificial intelligence (AI) is the future, but professionals may wonder what is ChatGPT’s role in offensive cybersecurity. Artificial intelligence (AI) enhances defensive and offensive cybersecurity measures, creating a secure cyber environment. Cybersecurity experts can leverage AI like ChatGPT for various purposes, including data analysis, vulnerability scanning, threat detection, and mitigation strategy development. AI strengthens access control and user authentication capabilities. Furthermore, AI can help with security automation and incident response.